Security
Our Commitment to Security & Compliance
At Suger, our mission is to simplify the sales integration & operation on multi cloud marketplaces for your organization, and that starts with ensuring the privacy of your data. To honor our commitment, we want to empower you to know how your data is used and protected throughout its entire lifecycle.
Security by Default
Suger designs and builds our products from the ground up with privacy and security in mind. We want our customers to feel reassured that their data is safe with us, so we strive to offer transparency about our processing of personal data. For information about how Suger processes personal data as a data controller, see our privacy policy. We also focused on implementing key data security protections from its inception. We implement technical and organizational measures aimed at assuring the security, integrity, and confidentiality of our customers’ data.
Infrastructure Security
- Data Encryption
All customer data is encrypted with TLS 1.2+ in transit and AES-256 at rest. Your passwords are salted and hashed using bcrypt. We use tools like Amazon Web Service’s Key Management System (KMS) to manage encryption keys using hardware security modules for maximum security in line with industry best practices. - Firewalls
AWS VPC, private subnet, and security group rules are leveraged to control network traffic. Application-level ingress and egress filtering are implemented to control inbound and outgoing traffic. - Service Management
We deploy our services using containers run on AWS managed EKS, meaning we typically do not manage servers or EC2 instances in production.
Application Security
- Secure Software Development
Secure SDLC processes, including threat modeling, design reviews, code reviews, SCA, and manual QA are implemented to keep the product free of bugs. - Vulnerability Management
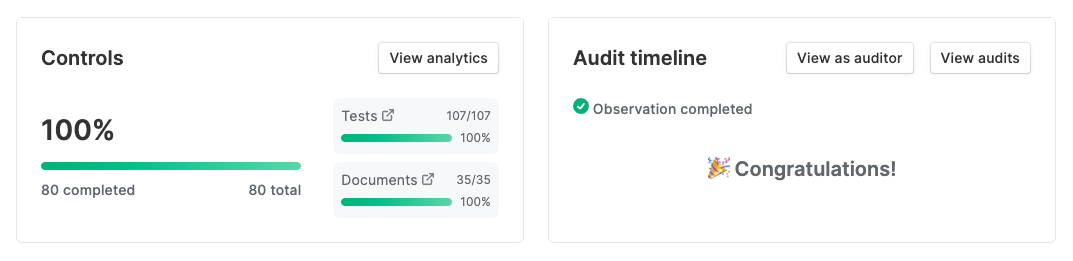
Suger uses AWS Inspector, which is an automated vulnerability management service that continually scans our AWS workloads for software vulnerabilities and unintended network exposure. Here is our latest scan report.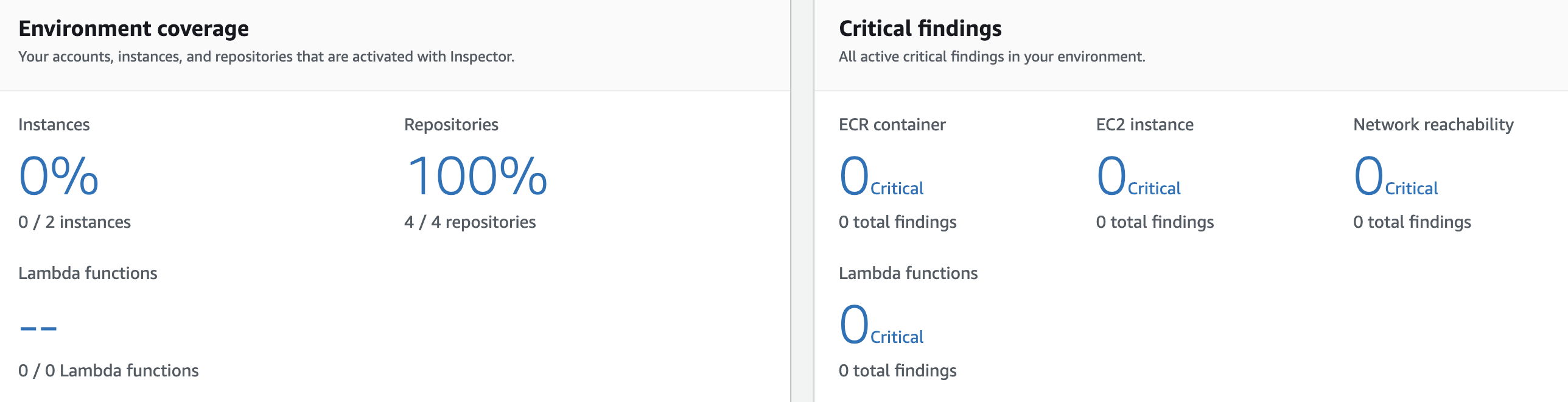
SOC 2
Yes, We are SOC 2 Type 2 audited. We worked with Vanta & Prescient Assurance to ensure our entire organization & services meet all requirements of AICPA SOC. If you need our SOC 2 report for security compliance, please feel free to contact us.
AWS Partner Qualified Software
By the Feb 6th 2023, Suger solution was reviewed by the AWS Foundational Technical Review (FTR) and got finally approved , which is valid for two years from the review date. Now we are proud of being AWS Partner Qualified Software 🎉 🎊.
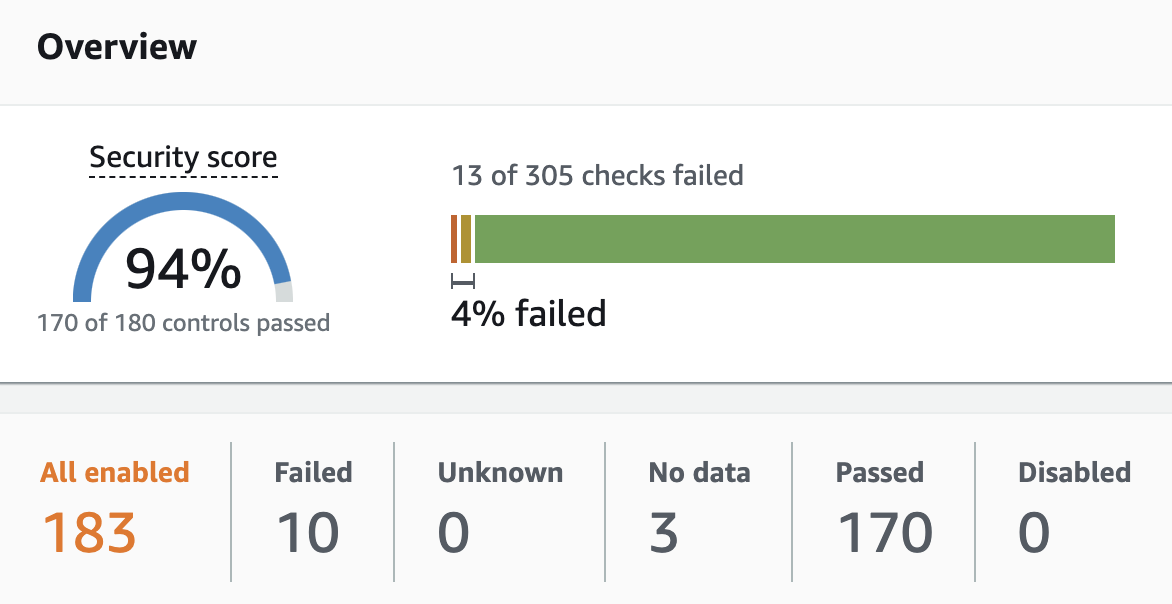
AWS Foundational Security Best Practices v1.0.0
The AWS Foundational Security Best Practices standard is a set of controls that detect when our deployed accounts and resources deviate from security best practices. This standard helps us continuously evaluate all of our AWS accounts and workloads, and quickly identify areas of deviation from best practices. It provides actionable and prescriptive guidance about how to improve and maintain organization’s security posture. Below is our score:
CIS AWS Foundations Benchmark v1.4.0
This is a set of security configuration best practices for Amazon Web Service (AWS), offer highly specific, detailed guidelines for implementing security controls in AWS services and validating their effectiveness. In addition to the AWS Foundations Benchmark, the Center for Internet Security (CIS) provides security guidance for specific AWS services, in the form of Product-Level Benchmarks and Standalone Cloud Service Benchmarks.
The CIS Benchmark addresses multiple aspects of AWS infrastructure and managed services, including operating systems, cloud service configuration, and network devices. By following CIS controls, organizations can protect their AWS deployments from known cyber attack vectors, to fulfill their part of the shared responsibility model.